Cyber risk exposes your weakest link: the remote worker

Cyberattacks are a massive threat in normal economies. They can bring your business to a full stop in a heartbeat. In a COVID-19 world, cyber security has become even more critical as suddenly remote workers test the IT infrastructure and unintentionally expose themselves to cyber criminals.
Our data shows just 46% of small and midsize businesses (SMBs) have an active, up to date, cybersecurity strategy. Yet, even the most advanced cyber technologies and strategies cannot protect against the weakest link — your employees. People have always been the weakest link of a layered cyber security strategy of people, process and technology in normal times. With knowledge workers functioning remotely from home offices, the threat and exposure is even greater.
You are most vulnerable when you are most vulnerable. Remote workers are working on their personal networks, outside of VPNs and beyond firewalls, increasing your risk and opening the door to increasingly sharper cyber criminals. On top of the issues and business challenges of functioning in the COVID world, what would the impact to your business be of having all your data held hostage? How would a massive ransomware attack and paying off the cyber criminals impact your cash flow, especially if you are one of the 33% of SMBs who have five months or less of cash on hand?
State of cybersecurity
The good news from the Q4 2019 Vistage CEO Confidence Index survey – which captured responses from 1,604 leaders of small and midsize businesses – was that cyber security awareness was on the rise. The bad news? So were cyber incidents.
In that survey, nearly a third (32%) of CEOs indicated that they had been a victim of a cyberattack in the last 12 months, an increase from 27% the prior year and 24% that reported attacks two years ago. That number is rising for two reasons, the first because cyberattacks are on the rise, but more significantly is that companies are more aware of these efforts of cyber criminals and bad actors due to the growing priority to protect their company’s data.
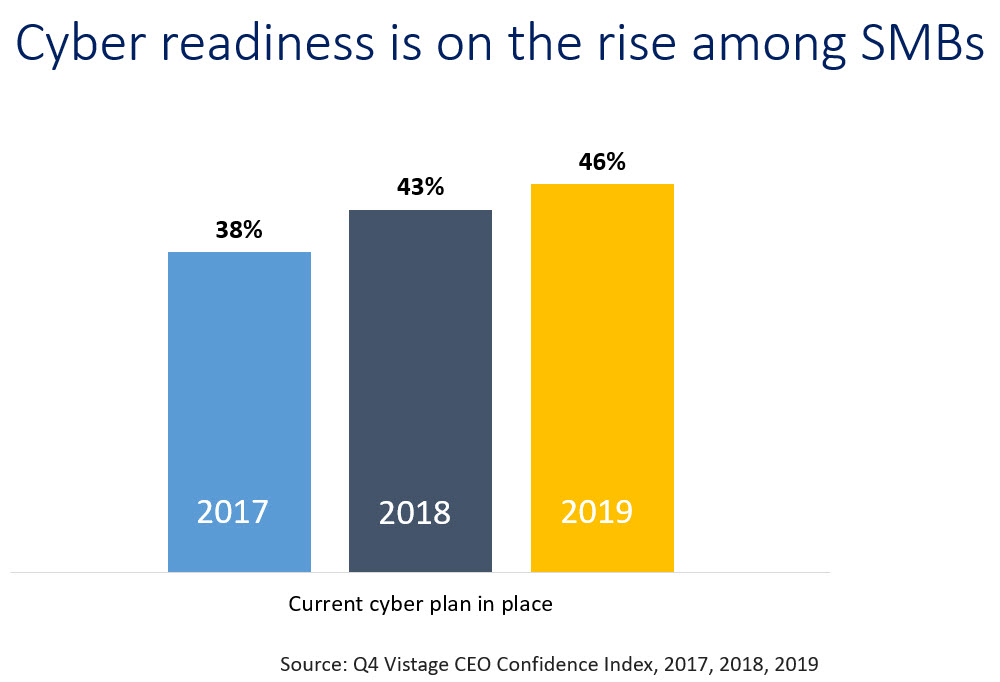
But the better news was that 46% of CEOs reported having an active, up-to-date cyber plan, which is an increase from 43% in 2018 and 38% in 2017. Those that were completely unprotected declined; just 22% reported not having a plan at all, down from 25% in 2018 and 27% in the Q4 2017 survey. Projections for 2020 is that these numbers have continued to increase, and SMBs have a greater level of protection than ever. We’ll learn more when we survey our CEO community in December 2020.
As businesses ramp up on their cyber awareness, bad actors are also ramping up on their criminal efforts. An annual review of the cybersecurity plan is necessary, reviewing each of the three components of people, process and technology. But by far, the biggest focus should be the weakest link — people.
Addressing the weakest link
Bringing awareness and training to employees is critical to address vulnerabilities that are caused by people. Since three-quarters of all cyberattacks or data breaches start with a phishing attempt or an error that happens at the user level, training your employees in cybersecurity will go a long way toward mitigating your risk for an attack.
There are many ways to approach training — and many economical solutions that cost less than $100 per employee. Here’s what the experts recommend:
- Train employees to abide by basic security principles. Establish basic security practices, such as using strong passwords, maintaining appropriate internet use, and handling customer information and data with care.
- Build a security consciousness. Consider using internal phishing simulations to teach people how to spot common signs of an attack.
- Invest in a stock test package. Similar to the simulation tool, this training will teach employees how to spot email scams and to evaluate whether a link is suspicious.
- Crosstrain employees. Give employees the opportunity to shadow IT personnel so you can build a team of unofficial deputy IT managers. This also creates more redundancy in your security by spreading out responsibility.
- Communicate why security matters. Help your employees understand why this training is important and what’s at stake for the company. Get past legal language and make it personal.
- Hire a fractional CIO. If you’re on a budget, use a fractional (contract or third-party service provider) model to get IT experts when you need them.
Mitigating risk from the remote workforce
The “Work from Home” (WfH) phenomena quickly took hold as organizations scrambled to adapt to the pandemic. In our April survey, 91.8% of organizations had implemented some form of WfH. While 42% of SMBs have begun to return to work, according to our most recent survey in October, 17% don’t expect to return until sometime in 2021 and another 11% are uncertain when they will go back.
It’s clear a hybrid model is emerging for WfH, allowing flexibility for those capable of WfH. Almost 5% were already a virtual organization or are planning to stay remote as a permanent solution. For many Millennials and Gen Xers in the workforce, WfH is not a perk, but a requirement as they seek to align and integrate their work and personal lives.
Remote workers create a broader threat landscape for small and midsize businesses. They are isolated and also vulnerable to the attempts of bad actors. “It’s important that remote employees understand the risks as well as how they can keep the company safe,” says Carla Stone, CEO of Tech Guard. “Employees should be expected to follow password guidelines, log in using a VPN and ensure their Wi-Fi is secure.” Other behaviors that should be required are found in this remote security checklist published by TechGuard. Many of these require processes implemented by a centralized IT effort.
Protecting the remote workforce carries additional risks that must be mitigated. Cyber training and awareness must be retrained and reinforced for those now in a WfH environment. Password protocols are more important than ever as home network security is not as robust as corporate networks. Consider implementing VPN networks if not already in place to beef up security and compliance. Make sure all software is kept up to date. Eliminate personal devices if possible and ensure data backup is taking place regularly. Think about adding cyber insurance. It won’t stop attacks but it will provide some layer of financial protection in case a ransomware attack takes away your data.
There is no question the WfH genie is out of the bottle. Once the pandemic has passed, a hybrid model will emerge for many businesses allowing flexibility for employees to WfH or the office. Advances in collaboration and video exchange applications have made distributed workforces possible. The rapid behavior changes, transformations and acceptance of WfH has broken down both generational and emotional barriers to this style of work. The benefits and flexibility of WfH are only possible if the data and communications that enable it are fully protected.

